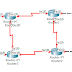
Kali ini saya akan membagi kalian tentang cara atau bagaimana mengkonfigurasi router dengan menggunakan RIP. Sebelum kita konfigurasi sebaiknya kita lihat desain yang mau di konfigurasi kalau saya ini yang mau di konfigurasi.
Oke ini desain yang akan saya konfigurasi, tanda titik merah adalah untuk mengetahui bahwa itu belum pernah di konfigurasi. Langsung aja deh kayaknya udah gak pada sabar.. hehehe
Pertama tentuin dulu ip address pada masing-masing kabel. misal saya ngambil contoh :
Router0 ke Router1 : 10.0.0.0/8
Router1 ke Router2 : 40.0.0.0/8
Router2 ke Router3 : 30.0.0.0/8
Router3 ke Router0 : 20.0.0.0/8
Router0 ke pc : 192.168.0.0/24
Router1 ke pc : 130.130.0.0/16
Router2 ke pc : 50.0.0.0/8
Router3 ke pc : 200.200.200.0/24
Setelah kita menentukan IP address barulah kita masuk tahap konfigurasi. berikut konfigurasinya :
Untuk Router0
Router>enable
Router#configure terminal
Router(config)#interface Serial2/0
Router(config-if)#ip address 10.10.10.1 255.0.0.0
Router(config-if)#clock rate 9600
Router(config-if)#no shutdown
Router(config-if)#exit
Router(config)#interface Serial3/0
Router(config-if)#ip address 20.20.20.1 255.0.0.0
Router(config-if)#clock rate 9600
Router(config-if)#no shutdown
Router(config-if)#exit
Router(config)#interface FastEthernet0/0
Router(config-if)#ip address 192.168.0.1 255.255.255.0
Router(config-if)#no shutdown
Router(config-if)#exit
Router(config)#
Untuk Router1
Router>enable
Router#configure terminal
Router(config)#interface Serial2/0
Router(config-if)#ip address 10.10.10.2 255.0.0.0
Router(config-if)#clock rate 9600
Router(config-if)#exit
Router(config)#interface Serial3/0
Router(config-if)#ip address 40.40.40.1 255.0.0.0
Router(config-if)#clock rate 9600
Router(config-if)#no shutdown
Router(config-if)#exit
Router(config)#interface FastEthernet0/0
Router(config-if)#ip address 130.130.130.1 255.255.0.0
Router(config-if)#no shutdown
Router(config-if)#exit
Router(config)#
Untuk Router2
Router>enable
Router#configure terminal
Router(config)#interface Serial2/0
Router(config-if)#ip address 40.40.40.2 255.0.0.0
Router(config-if)#clock rate 9600
Router(config-if)#no shutdown
Router(config-if)#exit
Router(config)#interface Serial3/0
Router(config-if)#ip address 30.30.30.2 255.0.0.0
Router(config-if)#no shutdown
Router(config-if)#clock rate 9600
Router(config-if)#exit
Router(config)#interface FastEthernet0/0
Router(config-if)#ip address 50.50.50.1 255.0.0.0
Router(config-if)#no shutdown
Router(config-if)#exit
Router(config)#
Untuk Router3
Router>enable
Router#configure terminal
Router(config)#interface Serial2/0
Router(config-if)#ip address 20.20.20.2 255.0.0.0
Router(config-if)#clock rate 9600
Router(config-if)#no shutdown
Router(config-if)#exit
Router(config)#interface Serial3/0
Router(config-if)#ip address 30.30.30.1 255.0.0.0
Router(config-if)#clock rate 9600
Router(config-if)#no shutdown
Router(config-if)#exit
Router(config)#interface FastEthernet0/0
Router(config-if)#ip address 200.200.200.1 255.255.255.0
Router(config-if)#no shutdown
Router(config-if)#exit
Router(config)#
Tahap memasukan ip pada routernya selesai kemudian masuk ke tahap Routing RIP berikut penjelasannya :
Untuk Router0
Router(config)#router rip
Router(config-router)#network 10.0.0.0
Router(config-router)#network 20.0.0.0
Router(config-router)#network 192.168.0.0
Router(config-router)#exit
Router(config)#exit
Router#write
Building configuration...
[OK]
Router#
Untuk Router1
Router(config)#router rip
Router(config-router)#network 10.0.0.0
Router(config-router)#network 40.0.0.0
Router(config-router)#network 130.130.0.0
Router(config-router)#exit
Router(config)#exit
Router#write
Building configuration...
[OK]
Router#
Untuk Router2
Router(config)#router rip
Router(config-router)#network 30.0.0.0
Router(config-router)#network 40.0.0.0
Router(config-router)#network 50.0.0.0
Router(config-router)#exit
Router(config)#exit
Router#write
Building configuration...
[OK]
Router#
Untuk Router3
Router(config)#router rip
Router(config-router)#network 20.0.0.0
Router(config-router)#network 30.0.0.0
Router(config-router)#network 200.200.200.0
Router(config-router)#exit
Router(config)#exit
Router#write
Building configuration...
[OK]
Router#
Oke jika tahap diatas sudah dilalui dengan benar, tinggal mengetestnya saja pada ping di komputer clientnya. masukan IP address sesuai dengan line pada routernya. misal :
PC0 : 200.200.200.2/24 gateway 200.200.200.1
PC1 : 192.168.0.2/24 gateway 192.168.0.1
PC2 : 50.50.50.2/8 gateway 50.50.50.1
PC3 : 130.130.130.2/16 gateway 130.130.130.1
Jika pada ping menunjukan seperti ini :
Pinging 50.50.50.2 with 32 bytes of data:
Reply from 50.50.50.2: bytes=32 time=20ms TTL=125
Reply from 50.50.50.2: bytes=32 time=9ms TTL=125
Reply from 50.50.50.2: bytes=32 time=22ms TTL=125
Reply from 50.50.50.2: bytes=32 time=11ms TTL=125
Ping statistics for 50.50.50.2:
Packets: Sent = 4, Received = 4, Lost = 0 (0% loss),
Approximate round trip times in milli-seconds:
Minimum = 9ms, Maximum = 22ms, Average = 15ms
Maka konfigurasi yang anda lakukan berhasil... Sekain posting kali ini semoga bermanfaat bagi pembaca.. See you next posting - http://tkjonline.net
Oke ini desain yang akan saya konfigurasi, tanda titik merah adalah untuk mengetahui bahwa itu belum pernah di konfigurasi. Langsung aja deh kayaknya udah gak pada sabar.. hehehe
Pertama tentuin dulu ip address pada masing-masing kabel. misal saya ngambil contoh :
Router0 ke Router1 : 10.0.0.0/8
Router1 ke Router2 : 40.0.0.0/8
Router2 ke Router3 : 30.0.0.0/8
Router3 ke Router0 : 20.0.0.0/8
Router0 ke pc : 192.168.0.0/24
Router1 ke pc : 130.130.0.0/16
Router2 ke pc : 50.0.0.0/8
Router3 ke pc : 200.200.200.0/24
Setelah kita menentukan IP address barulah kita masuk tahap konfigurasi. berikut konfigurasinya :
Untuk Router0
Router>enable
Router#configure terminal
Router(config)#interface Serial2/0
Router(config-if)#ip address 10.10.10.1 255.0.0.0
Router(config-if)#clock rate 9600
Router(config-if)#no shutdown
Router(config-if)#exit
Router(config)#interface Serial3/0
Router(config-if)#ip address 20.20.20.1 255.0.0.0
Router(config-if)#clock rate 9600
Router(config-if)#no shutdown
Router(config-if)#exit
Router(config)#interface FastEthernet0/0
Router(config-if)#ip address 192.168.0.1 255.255.255.0
Router(config-if)#no shutdown
Router(config-if)#exit
Router(config)#
Untuk Router1
Router>enable
Router#configure terminal
Router(config)#interface Serial2/0
Router(config-if)#ip address 10.10.10.2 255.0.0.0
Router(config-if)#clock rate 9600
Router(config-if)#exit
Router(config)#interface Serial3/0
Router(config-if)#ip address 40.40.40.1 255.0.0.0
Router(config-if)#clock rate 9600
Router(config-if)#no shutdown
Router(config-if)#exit
Router(config)#interface FastEthernet0/0
Router(config-if)#ip address 130.130.130.1 255.255.0.0
Router(config-if)#no shutdown
Router(config-if)#exit
Router(config)#
Untuk Router2
Router>enable
Router#configure terminal
Router(config)#interface Serial2/0
Router(config-if)#ip address 40.40.40.2 255.0.0.0
Router(config-if)#clock rate 9600
Router(config-if)#no shutdown
Router(config-if)#exit
Router(config)#interface Serial3/0
Router(config-if)#ip address 30.30.30.2 255.0.0.0
Router(config-if)#no shutdown
Router(config-if)#clock rate 9600
Router(config-if)#exit
Router(config)#interface FastEthernet0/0
Router(config-if)#ip address 50.50.50.1 255.0.0.0
Router(config-if)#no shutdown
Router(config-if)#exit
Router(config)#
Untuk Router3
Router>enable
Router#configure terminal
Router(config)#interface Serial2/0
Router(config-if)#ip address 20.20.20.2 255.0.0.0
Router(config-if)#clock rate 9600
Router(config-if)#no shutdown
Router(config-if)#exit
Router(config)#interface Serial3/0
Router(config-if)#ip address 30.30.30.1 255.0.0.0
Router(config-if)#clock rate 9600
Router(config-if)#no shutdown
Router(config-if)#exit
Router(config)#interface FastEthernet0/0
Router(config-if)#ip address 200.200.200.1 255.255.255.0
Router(config-if)#no shutdown
Router(config-if)#exit
Router(config)#
Tahap memasukan ip pada routernya selesai kemudian masuk ke tahap Routing RIP berikut penjelasannya :
Untuk Router0
Router(config)#router rip
Router(config-router)#network 10.0.0.0
Router(config-router)#network 20.0.0.0
Router(config-router)#network 192.168.0.0
Router(config-router)#exit
Router(config)#exit
Router#write
Building configuration...
[OK]
Router#
Untuk Router1
Router(config)#router rip
Router(config-router)#network 10.0.0.0
Router(config-router)#network 40.0.0.0
Router(config-router)#network 130.130.0.0
Router(config-router)#exit
Router(config)#exit
Router#write
Building configuration...
[OK]
Router#
Untuk Router2
Router(config)#router rip
Router(config-router)#network 30.0.0.0
Router(config-router)#network 40.0.0.0
Router(config-router)#network 50.0.0.0
Router(config-router)#exit
Router(config)#exit
Router#write
Building configuration...
[OK]
Router#
Untuk Router3
Router(config)#router rip
Router(config-router)#network 20.0.0.0
Router(config-router)#network 30.0.0.0
Router(config-router)#network 200.200.200.0
Router(config-router)#exit
Router(config)#exit
Router#write
Building configuration...
[OK]
Router#
Oke jika tahap diatas sudah dilalui dengan benar, tinggal mengetestnya saja pada ping di komputer clientnya. masukan IP address sesuai dengan line pada routernya. misal :
PC0 : 200.200.200.2/24 gateway 200.200.200.1
PC1 : 192.168.0.2/24 gateway 192.168.0.1
PC2 : 50.50.50.2/8 gateway 50.50.50.1
PC3 : 130.130.130.2/16 gateway 130.130.130.1
Jika pada ping menunjukan seperti ini :
Pinging 50.50.50.2 with 32 bytes of data:
Reply from 50.50.50.2: bytes=32 time=20ms TTL=125
Reply from 50.50.50.2: bytes=32 time=9ms TTL=125
Reply from 50.50.50.2: bytes=32 time=22ms TTL=125
Reply from 50.50.50.2: bytes=32 time=11ms TTL=125
Ping statistics for 50.50.50.2:
Packets: Sent = 4, Received = 4, Lost = 0 (0% loss),
Approximate round trip times in milli-seconds:
Minimum = 9ms, Maximum = 22ms, Average = 15ms
Maka konfigurasi yang anda lakukan berhasil... Sekain posting kali ini semoga bermanfaat bagi pembaca.. See you next posting - http://tkjonline.net
















![[Image: nmap-portscanning-08.JPG]](http://www.petri.co.il/images/nmap-portscanning-08.JPG)